To provide some greater transparency, we are disclosing what we
currently know about which chips that have suffered some sort of anomaly
either before or after acquisition.
Warning: graphic content. Viewer discretion is advised.
Summary
Chips are:
- #1 (Gigas MKIII, 8748): EA blown. Presumably this was done at factory *2
- #7 (Joshi Volley Ball AA-002 "NEC 015", ULA): scratched during post-processing. We have a high resolution scan before the scratch
- #8 (Great Swordsman AA-017, 8041AH): severe die damage, believed to be pre-existing before decap. However, the ROM was mostly intact and was photographed
- #10 (Great Swordsman AA-013, 8741): severe leadframe damage. Additionally, some EPROM damage that will prevent a complete dump. *1 FIB should restore most bits but may be cost prohibitive
- #19 (Vimana, HD647180): minor bond wire defect
- #44 (Victorious Nine A16_18.IC53): package open. Needs damage assessment
- #45 (Tatakae Big Fighter, 8751H): severe leadframe damage, but die was intact. Repaired for dump
- #50 (Guardian A68_14, 68705P5): surface damage. EPROM / presume dead *1
- #57 (Prebillian 7.7K, 68705P5): loose when received, but no visual damage on cursory inspection
- #58 (Teki Paki, HD647180): minor bond wire defect
- #59 (Tokio A71_24.IC57, 68705P5): needs assessment
- #78 (Gals Panic CALC1, ASIC): overglass has some damage. Pre-existing before decap?
- #94 (Hyper Neo Geo 64 I/O controller - driving type, TMP87CH40N): bond pads corroded beyond repair *3
- #95 (Hyper Neo Geo 64 I/O controller - fighting type, TMP87CH40N): bond pads corroded beyond repair *3
- #96 (Hyper Neo Geo 64 I/O controller - shooting type, TMP87PH40AN): bond pads partially corroded. We were unable to repair it, but did extract some crude dumps *1
- #102 (Fire Shark, HD647180): minor bond wire defect
- #104 (Crazy Fight, ULA): bond wires damaged during decap ultimately due to special silicone passivation. Theoretically could be re-bonded
- #123 (Bonze Adventure, C-Chip): received partial chip (missing MCU...). The EPROM may be recoverable but probably not worth processing given we have a second chip
- #124 (Cookie & Bibis, 87C52): die surface damaged. EPROM / presume dead *1
- #145 (Croupier, PIC16C74): missing leadframe pin (easy fix)
- #195 (Tatsumi TX-1, EPROM): deep scratch. Presume dead *1
- Note: some confusion on this. Actually labeled "192" but believe its 195
- #196 (Tatsumi TX-1, EPROM): okay? Is this worth dumping without 195? Repairs will be time consuming
- #204 (Bad Dudes (EI31.9A), 8751): 5 pins missing. Bond wires in poor shape. May be able to repair
- #209 (Raiga (8749.7V), 8749): Doesn't read out. EA blown? *2
- #223 (Tecmo Knight and Wild Fang D8749.6V, D8749HC): Doesn't read out. EA blown? *2
- #227 (Action Hollywood, PIC16C57): minor leadframe pin (easy fix)
The following were processed successfully to the best of our knowledge but did not result in good dumps:
- #139: some bit lines appear to be damaged. Observed before decap (per leaky PIC protection). Unknown root cause.
- #227: first 0x40 words are 0x000. Observed before decap (per leaky PIC protection)
*1: theoretically EPROMs can be read with with things like AFM / SEM. We haven't researched extensively but it sounds difficult
*2 we will research a workaround
*3 may be able to stain ROM. While we've had success before, its unpredictable and would require additional practice before attempting one of these
Gallery
In more graphic detail....
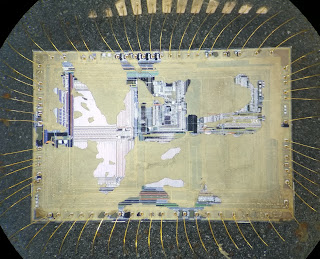
#1 blown EA:
#8 cracked die:
#10 leadframe:
#10 damaged EPROM:
#19, 58, 102 typical defect:
#19, 58, 102 typical repair:
#44:
#45 as received:
#45 after repair:
#50 general condition:
close up of damage:
#57 looks okay:
#59:
#78 overglass damage can be barely seen here:
#94 typical corrosion:
#95 showing corrosion + leadframe delaminating:
#96 as received:
Its also corroded, but not as bad. So we tried to touch up with epoxy:
but were ultimately unable to save the chip.
#104 pre-milling revealed special construction (silicone?):
This was very difficult to remove. Nitric acid softened but did not remove it:
After multiple acid and mechanical cycles was able to expose the die:
#123 as received:
We only have the SRAM, EPROM, and ASIC (no MCU). Additionally, chips have damage. For example, here are EPROM power pads:
This chip is basically considered a write off. However, since we had nothing to lose, we attempted to power up the EPROM using silver conductive epoxy:
Which worked! But it would require quite a few more connections to actually read out data. Given the die also has damage that may prevent readout, effort is probably better spent on other projects. This was, however, useful practice for the #45 repair.
#124 has some surface damage that likely makes it inoperable:
#195 ("192"):
Closing remarks
While decapping can produce great results, exposed dies are extremely fragile and require the utmost care. To that end, all samples have been packaged in appropriate containers to keep them safe. Its regrettable that some samples were damaged, but its unfortunately an inherent risk in this type of work.
Special packages can be difficult to deal with. We generally deal with them by acquiring expendable test samples and practicing until we are happy with the process. But, if we don't know what we have, we make a best effort and deal with situations as they come up. While failures are disappointing, they are carefully studied as a lesson for future work.
Hopefully this post didn't alarm people too much. First, hope it provides some more clarity on which chips were recovered vs which may actually produce a dump. Second, while
discomforting, we'd like to set realistic expectations that sometimes things don't
work out.
On a lighter note, look forward to our upcoming post on dumping the PIC16C57s!